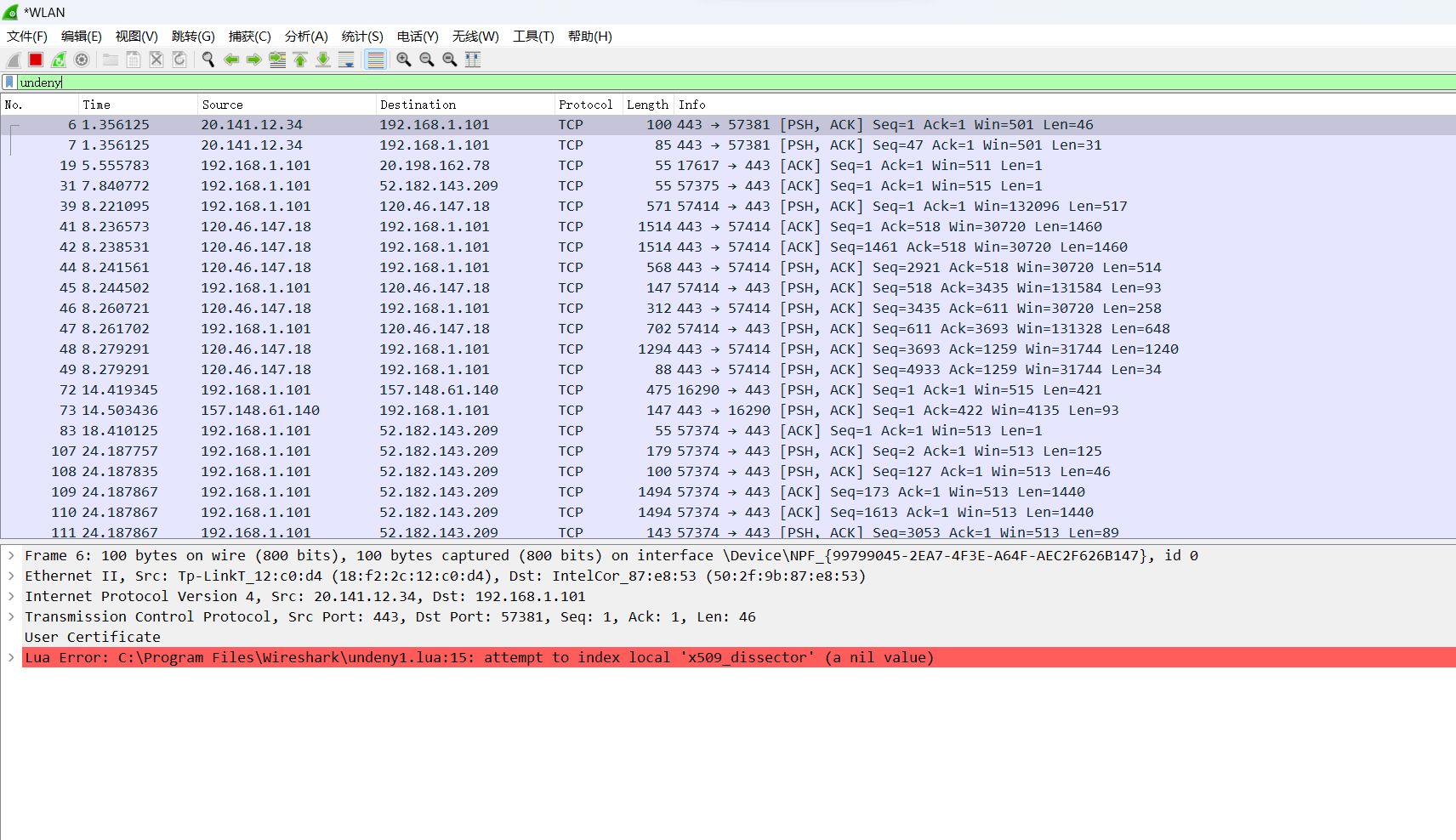
本周计划完成任务
本人所负责的不可否认性模块全部代码的初步编写
本周实际完成情况
通过解析数据,获取证书信息
相关代码
local version_str = string.match(_VERSION, "%d+[.]%d*")
local version_num = version_str and tonumber(version_str) or 5.1
local bit = (version_num >= 5.2) and require("bit32") or require("bit")
-- create a new dissector to decode rtp private payload
local NAME1 = "undeny"
local PORT = 5004
local RTP_PROTO_TYPE = 106
local undeny = Proto(NAME1, "undeny Protocol")
-- create fields of undeny
fields_M = ProtoField.uint8 (NAME1 .. ".M", "M", base.HEX,Payload_type,0x80)
fields_pt = ProtoField.uint8 (NAME1 .. ".PT", "PT", base.DEC,Payload_type,0x7F)
fields_seqno = ProtoField.uint16(NAME1 .. ".seqno", "Sequence number")
fields_h264bytes = ProtoField.bytes(NAME1 .. ".bytes", "H264Data")
fields_fec = ProtoField.bytes(NAME1 .. ".fec", "FEC Payload")
undeny.fields = { fields_M, fields_pt, fields_seqno, fields_h264bytes,fields_fec }
local RTP_dis = Dissector.get("rtp")
local H264_dis = Dissector.get("h264")
local Data_dis = Dissector.get("data")
-- dissect packet
function undeny.dissector(tvb, pinfo, tree)
length = tvb:len()
if length == 0 then return end
-- decode private header
local subtree = tree:add(undeny, tvb(0,3))
subtree:add(fields_M, tvb(0,1))
subtree:add(fields_pt, tvb(0,1))
subtree:add(fields_seqno, tvb(1,2))
-- show protocol name in protocol column
pinfo.cols.protocol = undeny.name
local fec_id = tvb(0,1):uint()
local fec_type = bit.band(fec_id,0x7F)
if fec_type == 109 then
tree:add(fields_fec,tvb(3))
else
H264_dis:call(tvb(3):tvb(), pinfo, tree)
end
end
--decode first layer as rtp
local udp_dissector_table = DissectorTable.get("udp.port")
udp_dissector_table:set(PORT,RTP_dis)
-- register this dissector
-- DissectorTable.get("rtp.pt"):add(PORT, undeny)
--decode private protocol layer 3-bytes private datas + standard h264
local rtp_dissector_table = DissectorTable.get("rtp.pt")
rtp_dissector_table:set(RTP_PROTO_TYPE,undeny)
do
local undeny_proto = Proto("undeny", "Undeny Protocol")
local f_user_certificate = ProtoField.bytes("undeny.certificate", "User Certificate")
undeny_proto.fields = { f_user_certificate }
function undeny_proto.dissector(buffer, pinfo, tree)
local length = buffer:len()
if length == 0 then return end
local subtree = tree:add(undeny_proto, buffer(), "User Certificate")
local x509_dissector = Dissector.get("x509") -- 获取X.509解析器
x509_dissector:call(buffer, pinfo, tree) -- 调用X.509解析器来解析证书
local cert_data = buffer:string() -- 获取证书数据
if is_rsa_2048_certificate(cert_data) then
subtree:add(f_user_certificate, buffer(0, length)) -- 将证书添加到协议树中
subtree:append_text(" (RSA-2048)") -- 添加证书类型描述
else
subtree:add(f_user_certificate, buffer(0, length))
end
end
local tcp_port = DissectorTable.get("tcp.port")
tcp_port:add(443, undeny_proto) -- 将端口号改为443
end
未完成原因:感觉有点难,迈出第一步有点艰难,熟悉上手后会好很多
本周遇到的问题
代码载入wireshark后,出现如下报错:
Lua: Error during loading:C:\Program Files Wireshark\undeny1.lua:83: attempt toindex local tls dissector tab' (a nil value)stack traceback:
C: Program Files Wireshark undeny1.lua:83: inmain chunk[C]: in function 'dofile'C:\Program Files Wireshark init.lua:669: in main
chunk
询问GPT解答:
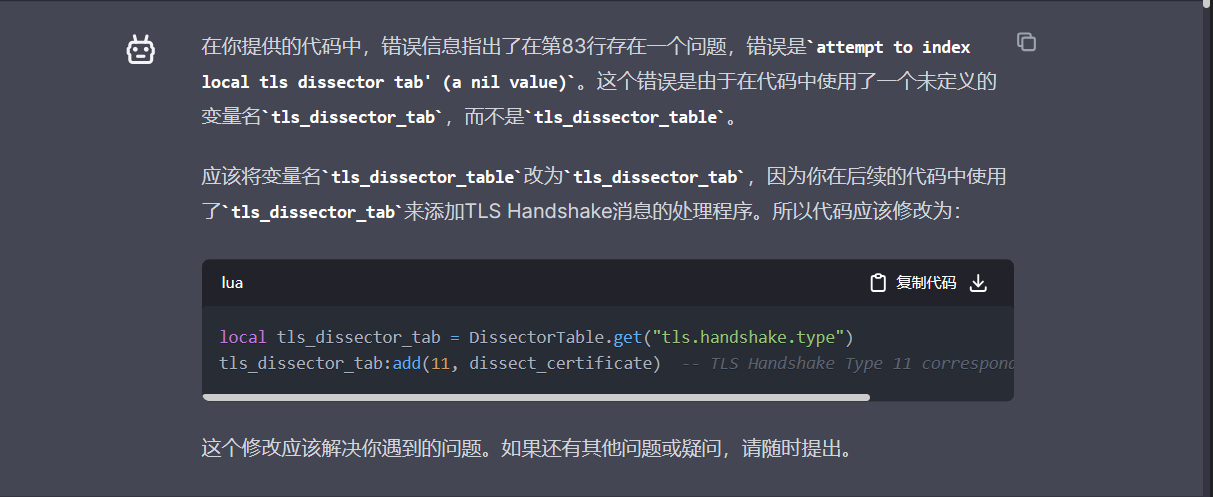
目前版本的插件载入后报错,过滤不到相应的包